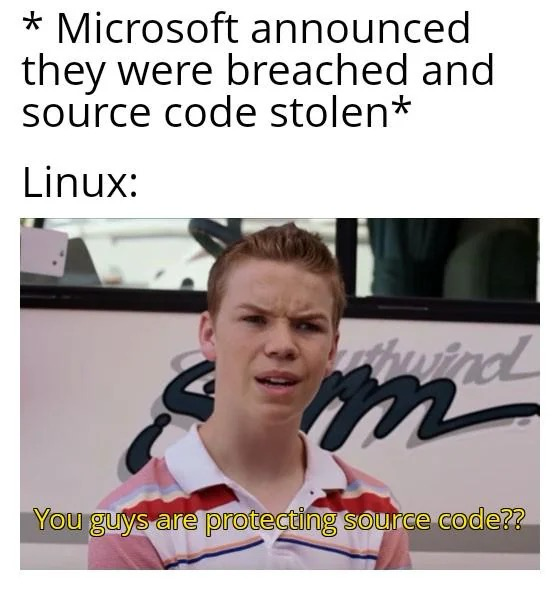
Is this a propaganda article to present closed-source software as more secure or is it to sell IT "security"?
»Open-Source Cybersecurity Is a Ticking Time Bomb:
A vast majority of the world's software runs on open-source code. Can it be secured?«
🔓 https://gizmodo.com/open-source-cybersecurity-is-a-ticking-time-bomb-1848790421
—
#opensource #cybersecurity #security #it #software #xz #foss #floss #itsecurity
OpenBSD was Right - Linux Kernel Developer Greg Kroah-Hartman
Original video: https://www.youtube.com/watch?v=jI3YE3Jlgw8
GrapheneOS version 2024050700 released:
https://grapheneos.org/releases#2024050700
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/12566-grapheneos-version-2024050700-released
You can find more talks here: https://cdn.gyptazy.ch/tech-talks/
#secinfo #security #secops #securitypatchmanagement #patchmanagement #debian #proxmox #freebsd #bsd #rockylinux
went down to the hotel lobby to retrieve my dinner delivery in a yoga outfit + snuggly cardigan + face mask.
some men with #RSAC2024 lanyards exited the elevator as I re-entered; they turned back to look at me and one said (very loudly, very pointedly staring at me) to the other, “I was like, did you hire me a hooker?”
if you are a man attending #rsac, please shut that kind of shit down when your peers do it. let’s not let insecurity rule our #security industry.
GrapheneOS version 2024050300 released:
https://grapheneos.org/releases#2024050300
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/12485-grapheneos-version-2024050300-released
From this week's Linux Update: Matthias Wübbeling shows you how to protect your data and operating system from prying eyes with @veracrypt https://www.linux-magazine.com/Issues/2024/279/VeraCrypt #encryption #VeraCrypt #security #privacy #containers #TrueCrypt #data
Reproducible builds - pros/cons
Instructor allowed me to quote his take on Pros and Cons of reproducible builds. Because, i found this very informative i want to share with others.
Original author: Nathan House (Station X)
"Reproducible builds involve a compilation process that generates the same binary or executable output for a given source code, regardless of the building environment. This approach offers various pros and cons when it comes to security, privacy, and anonymity.
Pros:
1. Trustworthiness: Reproducible builds ensure that the released binary is built from the published source code, allowing users to trust the software without having to compile it themselves.
2. Tamper detection: Any attempts to introduce backdoors or malware during the build process can be detected, as the output can be verified against the expected result.
3. Collaborative verification: Multiple parties can independently verify the builds, increasing confidence in the software's integrity.
4. Supply chain security: Reproducible builds can help mitigate supply chain attacks by ensuring the integrity of the code throughout the development, build, and distribution process.
Cons:
1. Increased complexity: Implementing reproducible builds can be complex and time-consuming, requiring consistent build environments and careful management of dependencies.
2. Limited scope: Reproducible builds only ensure the integrity of the build process and do not guarantee that the source code is free of vulnerabilities or malicious code.
3. False sense of security: Users may assume that reproducible builds imply that the software is entirely secure, while they only guarantee that the build process is consistent and hasn't been tampered with.
4. Overhead: Maintaining a reproducible build environment may introduce additional overhead for developers, potentially slowing down the development process.
Overall, reproducible builds can significantly enhance security, privacy, and anonymity in the software development process. However, their implementation requires careful planning and may introduce challenges and complexities that need to be managed effectively."
Does TLS sound like an ominous hiss to you? @mwl's #bsdcan TLS Tutorial on May 30th 2024 in #ottawa will enlighten you to core #internet #security tech and hint strongly at what could come back to bite you. https://indico.bsdcan.org/event/1/timetable/#20240530.detailed #tls #ssl #security #openbsd #freebsd #netbsd #networking
Today I've been really busy and I'm exhausted, but I wanted to share the "gem" of the day.
A colleague (whom I've never spoken to before) calls me and explains that they need to connect a client's server with their management system. To communicate, the client's server needs to be reachable via telnet. I explain that I can't open telnet to the world, but if necessary, I can set up a VPN of their choice (Wireguard, OpenVPN, even Zerotier if it's helpful) and grant telnet access through the VPN. Not ideal, but better than nothing...
That said, the colleague attacks me: "Here you are, with these VPNs - don't you understand they're used to spy on us? Governments intercept all VPNs to steal our personal data." I try to clarify that I may not have explained myself well and that I don't mean using the famous commercial VPNs, but a private VPN access to allow the two machines to communicate securely. No luck: "Haven't you realized yet? Every time we open a VPN, they know and intercept us."
Frankly, I was speechless...
#VPN #Privacy #Security #Misconceptions #IT #SysAdmin #ITHorrorStories
Aaah Monday. Time for a new intel #security #sideChannel attack https://pathfinder.cpusec.org/index_files/Pathfinder_HoseinYavarzadeh_ASPLOS24.pdf
I wonder how long it will be before Chinese researchers only report these to the CCP?
The global collaboration in #infosec and #tech in general is declining after Xi Jinping’s rise to power and blockages of free trade by successive US presidents.
[fixed URL]
Another bit of #security advice I'd like (boosts welcome). I have a need to share a bunch of passwords to stuff with some people. It's personal, not work. So I'm looking for a shared password vault/wallet.
From my perspective I want:
- Free
- Self hosted (maybe sync via nextcloud or NFS or something)
- has to work offline (this will have passwords to routers and things that we need to get even if servers are down)
- Cross platform (mac, linux, Windows)
- Mobile app desirable but sorta optional
I'm not too fussed if we have to be sorta clunky about "who has the most recent version" but synchronising is better.
eHealth: Nach Cyberangriff droht US-Bevölkerung großer Datenleak
Change Healthcare hat nach einem Cyberangriff zugegeben, Lösegeld gezahlt zu haben. Dieser soll das Unternehmen bereits 1 Milliarde US-Dollar gekostet haben.
Russian Sandworm hackers targeted 20 critical orgs in Ukraine https://www.bleepingcomputer.com/news/security/russian-sandworm-hackers-targeted-20-critical-orgs-in-ukraine/ #news #Security
I spent some time testing BSD Mail today.
I tried to crash the whole system, to see how stable Dovecot's replica is (spoiler: it's definitely reliable). I've made up my mind that passwords will be encrypted via bcrypt, ensuring modern, reliable, and secure cryptography.
From now on, it's possible to change your password through SOGo, which will update the DB where Dovecot and opensmtpd fetch their data from.
Let's move forward!
#BSDMail #Dovecot #OpenSMTPD #OpenBSD #FreeBSD #SOGo #Security #IT
🆕 blog! “I can't use my number pad for 2FA codes”
This has to be the most infuriating bug report I've ever submitted. I went to type in my 2FA code on a website - but no numbers appeared on screen. Obviously, I was an idiot and had forgotten to press the NumLock button. D'oh! I toggled it on and typed again. No numbers appeared. I […]
👀 Read more: https://shkspr.mobi/blog/2024/04/i-cant-use-my-number-pad-for-2fa-codes/
⸻
#HTML #javascript #security #ui #ux
Erst jetzt erfahren, dass die 'security.txt' Datei auf dem Web im '/.well-known/' Verzeichnis vom Host ist und nicht auf '/'. 🤒
No gut, mensch kann (darf) es auch im '/' hinterlegen ist aber mMn nicht so elegant. Das ist nun ohne jeglichem Aufwand verschoben aber weshalb wusste, sprich raffte, ich es bisher nicht?
—
#webdev #webserver #security #txt #securitytxt #webknown #server #web
Every version of the PuTTY tools from 0.68 to 0.80 inclusive has a critical vulnerability in the code that generates signatures from ECDSA private keys. Tthe effect of the vulnerability is to compromise the private key https://www.chiark.greenend.org.uk/~sgtatham/putty/wishlist/vuln-p521-bias.html #infosec #security #ssh #opensource #linux #unix #windows
Back door xz vulnerability has been officially reverted for @fedora 40 https://www.linux-magazine.com/Online/News/XZ-Gets-the-All-Clear #malare #XZBackdoor #Fedora #Ubuntu #ArchLinux #Linux #OpenSource #security #patch #Rawhide #FOSS
Hey! Let's talk about #SSH and #security!
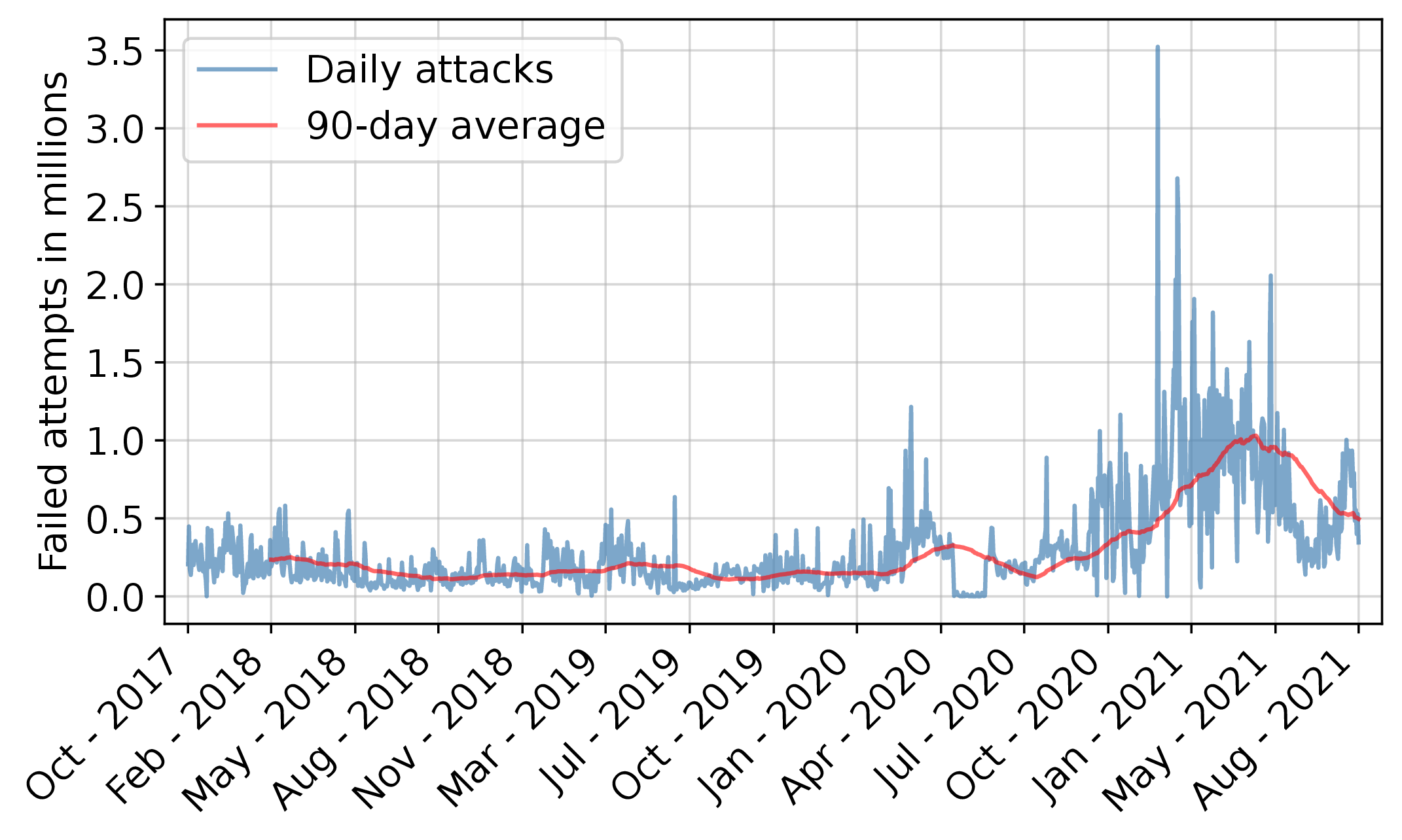
If you've ever looked at SSH server logs you know what I'm about to say: Any SSH server connected to the public Internet is getting bombarded by constant attempts to log in. Not just a few of them. A *lot* of them. Sometimes even dozens per second. And this problem is not going away; it is, in fact, getting worse. And attackers' behavior is changing.
The graph attached to this post shows the number of attempted SSH logins per day to one of @cloudlab s clusters over a four-year period. It peaks at about 3.4 million login attempts per day.
This is part of a study we did on our production system, using logs of more than 640 million login attempts, covering more than 1,500 hosts on our side and observing more than 840 thousand incoming IP addresses.
A paper presenting our analysis and a new, highly effective means to block SSH brute force attacks ("Where The Wild Things Are: Brute-Force SSH Attacks In The Wild And How To Stop Them") will be presented next week at #NSDI24 by @sachindhke . The full paper is at https://www.flux.utah.edu/paper/singh-nsdi24
Let's dive in. 🧵
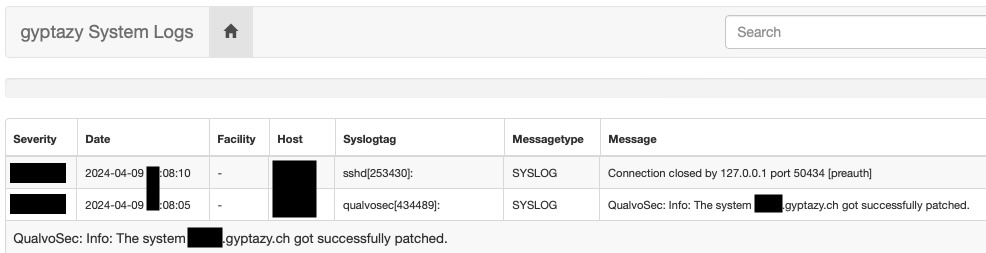
#SecurityPatchManagement tools like #QualvoSec may help integrating automated security patches.
#infosec #linux #BSD #Debian #RockyLinux #CentOS #RedHat #FreeBSD #patchManagement #SecurityPatching #Patching
I have no problem with Chromium and Firefox ported to FreeBSD.
This goodness is largely thanks to me being a billionaire, and spending swathes of money on secret miniaturisation of orphaned elks. You know, like in Fantastic Voyage in the 1960s, except these elks of mine become much, much smaller, small enough to fit in the Internet. My army of Internet elks fends off the Mozilla spies that fly over Wi-Fi into Firefox on other platforms.
Do I get thanked? Never.
#philanthropy #Ben #thetwoofusneedlooknomore #rats #cats #elks #Internet #security #Mozilla #Firefox #Google #Chrome #Chromium #Microsoft #Windows #BillGates #FreeBSD
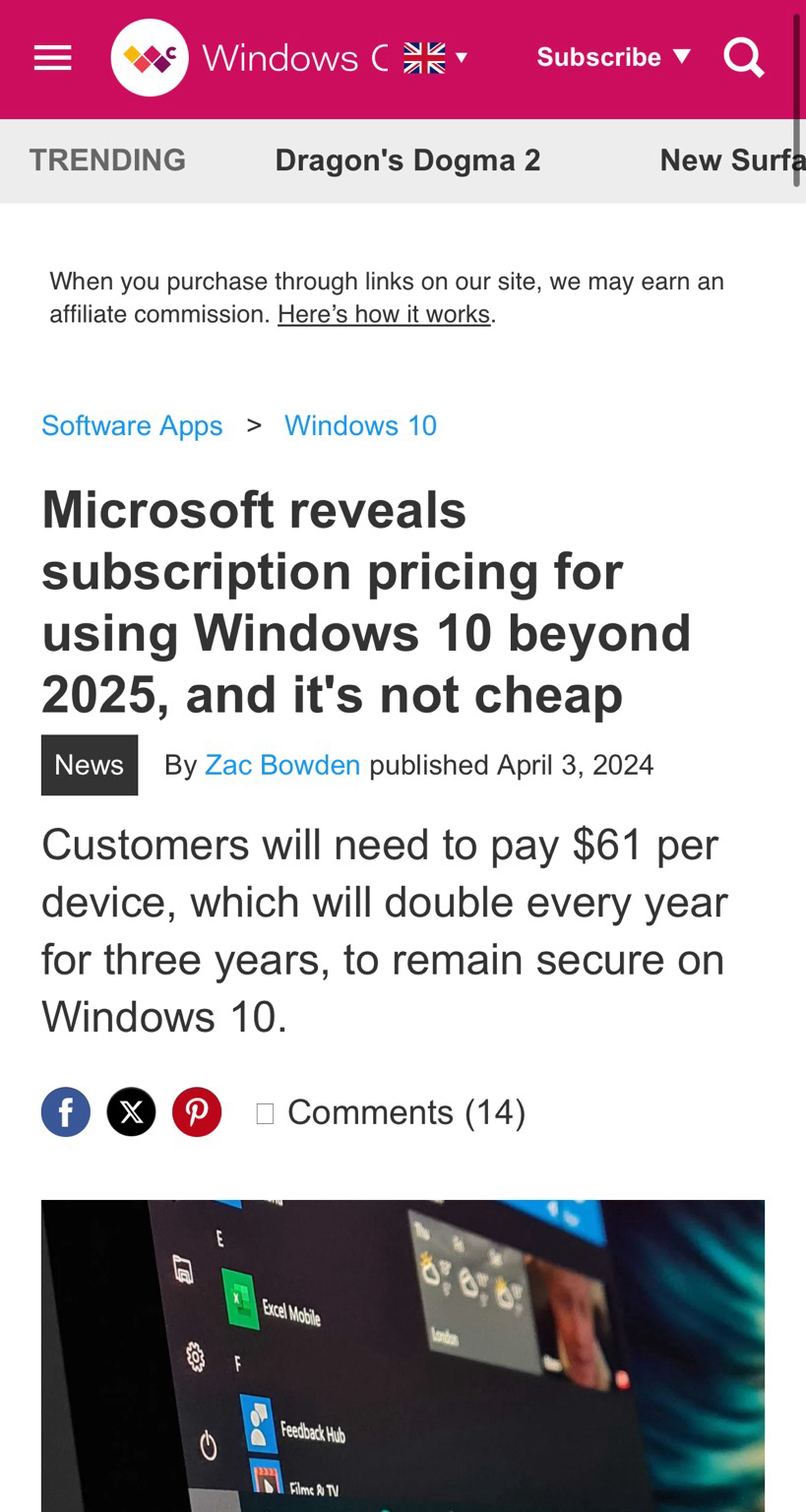
Microsoft reveals subscription pricing for using Windows 10 beyond 2025, and it's not cheap. Customers will need to pay $61 per device, which will double every year for three years, to remain secure on Windows 10. If you just do shopping or social media you can use alternative os like Ubuntu, Mint, or pop os for your older computer instead of jumping to windows 11. Also regardless of windows 10 or 11 prices you will still get Ads in Windows 😂 #linux #privacy #security Choose wisely
@emaste I see <https://forums.freebsd.org/posts/610565>, but still, this surprises me:
% ls -hln /var/db/locate.database
-r--r--r-- 1 65534 0 100M 7 Apr 00:01 /var/db/locate.database
% man -P cat security | grep locate
%
FreeBSD Foundation and Digital Security by Design (DSbD)
❝… CHERI and CheriBSD, developed to revolutionize hardware-based protection against memory safety vulnerabilities, were developed by a collaboration from researchers from the University of Cambridge, alongside corporate partners such as Google, Microsoft, Arm, and SRI International, and with support from the UK government. …❞
How the XZ backdoor works https://lwn.net/SubscriberLink/967192/6c39d47b5f299a23/ #linux #infosec #security
Great progress has been made last week for the Linux Audit blog: https://linux-audit.com/
Almost a full migration from WordPress to Hugo. Content moved, new logo, favicon changed, optimized web performance, load balanced web servers, files pre-compressed, redirects, monitoring, and more. A few things are left, such as converting some of the images and adding descriptions to all pages. After that, the content will get updated.
Any feedback or thoughts?
Uncommenting the "block in all", sending a pfctl -f /etc/pf.conf - noting in that precise moment that I didn't explicitly pass ssh - being closed out of my own server...done! ✅
#Networking #SysAdmin #Firewall #Security #SSH #ServerManagement #FreeBSD #OpenBSD
What Turmoil in #ECOWAS Means for #Nigeria and Regional #Stability
#BurkinaFaso, #Mali and N#iger have left ECOWAS, the regional bloc that sanctioned them after #military officers seized power in each. In this Q&A, #Crisis Group expert Nnamdi #Obasi assesses the import of these events for West #Africa’s #security architecture and #Nigeria’s #influence therein.
#economy #politics #geopolitics #Afrika #afrique #africa #افريقيا
This is one of the best explanations of the xz matter I have seen so far:
https://lcamtuf.substack.com/p/technologist-vs-spy-the-xz-backdoor
and it leads in with a quote to remember -
"This dependency existed not because of a deliberate design decisionby the developers of OpenSSH, but because of a kludge added by some Linux distributions to integrate the tool with the operating system’s newfangled orchestration service, systemd."
Enjoy!
I suppose everyone and their grandmother is now using the xz/sshd exploit to further their own agenda, so I am going to take this opportunity to further mine as well.
1. #Autotools are a bad build system. If configure scripts are completely unreadable, there should be no surprise that people won't notice obfuscated malicious code in there, provided that everything else is obfuscated by design.
2. Static linking and vendoring is bad. Do you know why the prompt #security response was possible? Because we just had to revert to older liblzma. We didn't have to check, patch and re-release hundreds of projects. It wouldn't be this easy with #RustLang and cargo.
3. You can blame #OpenSource for being underfunded and open to abuse in core system packages. However, no IT project can be resilient to a sufficiently powerful bad actor, and that it happened to xz is just an incident. Corporate projects aren't resilient to it, neither is proprietary, closed-source software.
So, embrace #Meson, embrace dynamic linking, embrace distribution packaging and donate to open source developers.
In light of the recent news about Vultr and its new (absurd) TOS, I'm seriously considering relaunching an email hosting service. I already have several hundred mailboxes in hosting and everything's fine, but I've always thought that with the big players in the game, it wasn't worth extending this service anymore.
Now I see potential, and it will be based exclusively on open-source technologies, accompanied by technical explanations on the setup and security of the entire system.
Soft Skills for Cyber Security (Employers Want to See)
by Spencer Abel
EXTREME CAUTION!!

"KDE advises extreme caution after theme wipes Linux user's files"
"It executes rm -rf on your behalf [and] deletes all personal data immediately. No questions asked. I canceled this when it asked for my root password, but it was too late for my personal data. All drives mounted under my user were gone, down to 0 bytes. [G]ames, configurations, browser data, [and the] home folder [are] all gone."
The #asiabsdcon 2024 #PF tutorial is done, *updated* slides as PDF at https://nxdomain.no/~peter/pf_asiabsdcon2024.pdf #openbsd #freebsd #networking #security #bsd #taipei
This week it's #asiabsdcon https://2024.asiabsdcon.org/program.html - I'll be doing a refresh of the "Network Management with the OpenBSD Packet Filter Toolset" tutorial with Max Stucchi @stucchimax #openbsd #freebsd #networking #pf #packetfilter #security #trickery
#Fujitsu is now on the list of companies that have suffered a #DataBreach of customer data. #security
https://techcrunch.com/2024/03/18/fujitsu-tech-giant-hacked-customer-data-breach/?guccounter=1
Henrietta Dombrovskaya kicking off #PostgreSQL @ #SCaLE21x Day 2 with "Securing Your PostgreSQL Data: A Comprehensive Guide to Protecting Your #Database Assets"
https://www.socallinuxexpo.org/scale/21x/presentations/securing-your-postgresql-data-comprehensive-guide-protecting-your-database
#security #openSource #databases #postgres
Ouch! AMS-IX is hit bad here 🤦♀️ 🥺 👩💻
“The Netherlands hosts some of the world’s largest internet exchanges. This obliges us to make the best use of these exchanges for our national security. With the Temporary Cyber Act, we will make optimum use of the data carried on our cables to protect The Netherlands against Russian and Chinese hackers” – Dutch government announcement
https://berthub.eu/articles/posts/dutch-intelligence-and-security-law/
#QualvoSec's upcoming features:
- whitelist (packages to update only)
- blacklist (package to refuse from being upgraded)
- API (list of installed packages & versions on nodes)
- Multiple patch windows
- Grouping
- First iteration of (the still very limited) admin tool
#patchmanagement #security #infosec #debian #freebsd #rockylinux #redhat #ubuntu #BSD #securitypatchmanagement #Fedora
🆕 blog! “I made a mistake in verifying HTTP Message Signatures”
It's never great to find out you're wrong, but that's how learning and personal growth happens. HTTP Message Signatures are hard1. There are lots of complex parts and getting any aspect wrong means certain death2. In a previous post, I wrote A simple(ish) guide to verifying …
👀 Read more: https://shkspr.mobi/blog/2024/03/i-made-a-mistake-in-verifying-http-message-signatures/
⸻
#ActivityPub #CyberSecurity #http #security
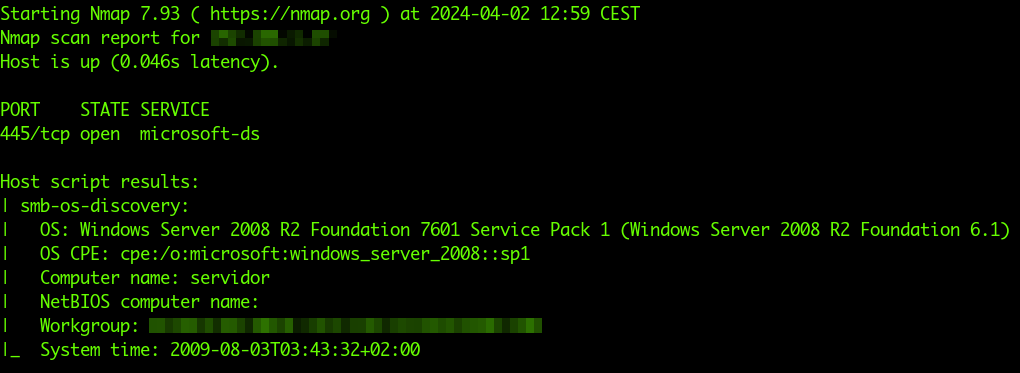
Me: "You need a new server. The current one is 14 years old, critical, and starting to show signs of fatigue and inadequacy."
Them: "No, make it work. At most, we'll add more RAM."
Me: "We should still upgrade it, and no, you can't keep running virtualized Windows Server 2008 indefinitely, even if it's only on the LAN. You need to plan an upgrade for the entire infrastructure."
Them: "No, we have no budget for this (after spending thousands of euros on purely aesthetic office redecorations for staff offices, which were already in excellent condition)."
Me: "It's about 3,000, maximum 4,000 euros - do you realize that if that server were to go down, the loss for you would be in those figures every hour of downtime? Maybe you don't worry about it, but I do, because I understand what you're risking."
Them: "Find a way to make the current hardware work stably so you can stop worrying."
Me: "Okay, I've found the solution. From now on, you can find yourselves a new consultant, because from now on, I've already stopped worrying about you."
Sometimes it's necessary, unfortunately.
Parrot OS is distribution like Kali but with different focus. It's great distro, and community forum is welcoming (and as i remember people are really helpful even for beginners)
Here is an interview with Lorenzo Palinuro and how the beginnings of this distro looked.
Very cool reading.
Unlike bloated solutions like #Spacewalk or #Landscape, this framework of QualvoSec is characterized by its minimalistic design, ensuring simplicity and ease of use. It operates entirely in Python, utilizing only a handful of imports to streamline the user experience.
https://gyptazy.ch/blog/qualvosec-a-minimalistic-security-patch-management-tools-for-linux-and-bsd/
#Ed25519 or #ECDSA-P256 or still on some #RSA algorithms? Shorter key length is especially in DNS a benefit but still not all resolvers may be able to support this in 2024?!
New Video from The Iron Sysadmin, on a new feature in FreeIPA that lets you login via a Yubikey instead of a password. Neat stuff.
On Youtube: https://youtu.be/2m9HfJE9pj8
Or if you'd prefer without the corporate spying: https://video.ironsysadmin.com/w/cQ1eX1sphxxvboFfrMwiM2
IT Security Weekend Catch Up – March 1, 2024
by badcyber
https://badcyber.com/it-security-weekend-catch-up-march-1-2024/
I am of course delighted to see people finding my #OpenBSD piece https://nxdomain.no/~peter/what_every_it_person_needs_to_know_about_openbsd.html, but I think the good people at #APNIC did an excellent job editing the thing into three more easily digestible chunks starting with https://blog.apnic.net/2021/10/28/openbsd-part-1-how-it-all-started/ #openbsd #needtoknow #security #internet
Beware infected #Github repositories having #malware in them.
https://apiiro.com/blog/malicious-code-campaign-github-repo-confusion-attack
> In order to maximize the chances of infection the malicious actor is flooding GitHub with malicious repos
Like this:
- Clone existing repos (for example: TwitterFollowBot, WhatsappBOT, discord-boost-tool, Twitch-Follow-Bot)
- Infect them with malware loaders
- Upload them back to GitHub with identical names
- Automatically fork each thousands of times
- Covertly promote them across the web
ONCD Leaders Call for a Memory Safe Future
https://www.whitehouse.gov/oncd/briefing-room/2024/02/26/video-technical-report-launch/
Link to technical report:
https://www.whitehouse.gov/wp-content/uploads/2024/02/Final-ONCD-Technical-Report.pdf
Additional reading:
"NSA Releases Guidance on How to Protect Against Software Memory Safety Issues"
"The Case for Memory Safe
Roadmaps"
https://www.cisa.gov/sites/default/files/2023-12/The-Case-for-Memory-Safe-Roadmaps-508c.pdf
Obligated periodic reminder
that I am currently Looking for Work! ✨
Remotely from Canada 🇨🇦
(ideally, but flexible)
At a great organization 💚
Related to one of those fields:
#Privacy #Security #Tech #DigitalRights #HumanRights #Python
Check this post for more details: https://infosec.exchange/@Em0nM4stodon/111054547728861638
#GetFediHired #FediHired #JobSearch #LookingForWork #JobsCanada #JobsCanadaLooking
"Is Port Scanning Legal?"
article by Nathan House and Gary Smith.
IT Security Weekend Catch Up – February 23, 2024
https://badcyber.com/it-security-weekend-catch-up-february-23-2024/
Why am I not surprised by this and why is IT & Internet security still not really taken seriously?
«Brussels spyware bombshell: Surveillance software found on officials’ phones. EU Parliament defense committee was the target of phone hacking, internal email says.»
– by @politico
🕵️ https://www.politico.eu/article/parliament-defense-subcommittee-phones-checked-for-spyware/
—
#eu #brussel #spyware #hack #email #itsec #internet #phone #software #security #europe #it #internet
Malware Statistics for 2024: Trends, Targets and Threat Actors
by Gary Smith
Almost all companies use #Microsoft #Exchange even though it has long been considered inaccurate and insecure among serious #professional's. You can see it again and again in the #news and serious #IT people regularly look at the #security messages following @CVE_Program on @cve one way or another.
📰 https://securityaffairs.com/159424/hacking/28000-vulnerable-microsoft-exchange-servers.html
👉 https://www.cve.org/CVERecord?id=CVE-2024-21410
I'm not so familiar with #AI and security on the #Internet that I really have a #clue. That's another reason why articles like this are very good for informing me and explaining it to customers. #WebSec is more than just #password and #secrecy.
«Post Quantum Cryptography: Why We Need Resistant Encryption NOW.
Quantum-resistant or post-quantum #cryptography is our best bet against attacks from upcoming quantum computers to increase #security and #privacy.»
– @Tutanota
The position lights from #Decathlon are not worth the money. After using them on my #SUP two times, they are already corroded internally. Didn't even dunk them into water, just the humidity and the cold.
Anyone has a better idea what lights I can have on my board, to make sure boats see it?
IT Security Weekend Catch Up – February 17, 2024
by badcyber
https://badcyber.com/it-security-weekend-catch-up-february-17-2024/
Backdoors that let cops decrypt messages violate human rights, EU court says
One of comments about the title:
"Contrary to what the headline says, the European Court of Human Rights in Strasbourg, France, is not an EU court. It is part of the Council of Europe, which is older than the EU and has more members, and is mainly concerned with human rights related issues.
The EU has its own Court, the Court of Justice of the European Union (CJEU) in Luxembourg.
Edit: just to add, the article gets all the nuances right and refers to the Council of Europe and even to possible endorsement by the CJEU, so the problem is only with the headline."
Another article + discussion https://news.ycombinator.com/item?id=39369653
«The religion of techno-optimism:
Tech billionaires are using faith to solidify their power»
– by @parismarx
This is also the reason why many people fall for it blindly and also why it is a secure income for those who sell it but are not necessarily sure what they are selling.
🤷 https://disconnect.blog/the-religion-of-techno-optimism/
—
#religion #tech #security #it #opinion
Goal - to be skilled researcher.
---------------------------
The following words form #security course helped me to set a goal.
"Only a small percentage are elite researchers, exploit developers, zero-day researchers, malware writers etc.
The majority are buyers, unsophisticated and less skilled."
Maybe starting with bug bounty isn't that bad idea?
---------------------------
#goal
Today i learned on #security course that "Reproducible builds" is a way to mitigate backdoor.
https://reproducible-builds.org/who/projects/
This makes sense for someone who uses binaries, but what if i use metadistribution? is it makes sense?
"the internet of s*** is out of control" by Low Level Learning
Coordinating and responsibly disclosing today’s two #DNSSEC #security vulnerabilities has been a huge coordination effort amongst researchers, #DNS implementers and early-access testing by our collective customers. It is a true testament to #OpenSource security and resilience. Our thanks go out to everyone involved! 💚🛡️💚 https://nlnetlabs.nl/projects/unbound/security-advisories/
🚨 We have released version 1.19.1 of Unbound #DNS resolver, which contains #security fixes for CVE-2023-50387 and CVE-2023-50868. ⚠️ Please update as soon as possible in order to mitigate two #DNSSEC validation vulnerabilities that affect all well-known resolvers. https://nlnetlabs.nl/news/2024/Feb/13/unbound-1.19.1-released/
<https://wiki.bsd.cafe/docs:freebsd:choose>
Choosing a version of FreeBSD – operating system branches, code quality, lifespans, and support [BSD Cafe Wiki]
Prominence to:
— the five-year support model.
The vertical timeline is intentionally simplified (excluding STABLE, excluding dates).
#FreeBSD #engineering #quality #support #errata #security #CURRENT #STABLE #RELEASE #lifespan #LTS
Current 2024 Top 10 List of Scams and Frauds
https://www.consumerfraudreporting.org/current_top_10_scam_list.php
@security #scam #security #social_engineering
#socialengineering
"You cannot ever had a hundred percent security, just like you can never have zero risk.
If you have ever seen someone advertising a hundred percent security, run a mile. They have no clue what they're talking about.
Unless you stop engaging in an activity, there'll always be risk."
oh hey y'all know this, anyway...
#platform #security starts with #hardware #documentation :)
^ should we print this on t-shirts? ^^





 🙀🚂🐧
🙀🚂🐧