Building a database management system from scratch ^-^
https://github.com/AnarchistHoneybun/rdms
Discussions: https://discu.eu/q/https://github.com/AnarchistHoneybun/rdms
I published my thoughts on
Long Term Rust Project Maintenance
https://corrode.dev/blog/long-term-rust-maintenance/
Did I forget anything?
Feedback welcome!
My rate for a Rust job is less than my rate for other languages.
Consider this to be not-having-to-debug-shit-at-3AM discount.
🦀 Rust participates in OSPP 2024 (limited to students)
👉 To encourage college students to participate in developing and maintaining open source software
👉 Student registration ends on the 3rd of June
Are you sick of the "dd" utility? Check out this TUI!
💽 **caligula**: A user-friendly, lightweight TUI for disk imaging
🔥 Burn & decompress files with cool graphs!
🚀 Supports verification & hash validation.
🦀 Written in Rust & built with @ratatui_rs
⭐ GitHub: https://github.com/ifd3f/caligula/
#rustlang #ratatui #tui #ratatui #disk #image #linux #terminal #decompress #validation
Am I missing something or is it basically impossible to have `cargo update` actually select dependencies that are acceptable for the specific minimal `rust-version`? Like, even if you install old #RustLang version, `cargo update` from this version will update `Cargo.lock` to dependencies that require a newer Rust version and render the package non-buildable?
So yeah, I suppose you either end up requiring newer Rust (but you don't really know which version, since you don't know what's the highest minimal requirement in your dependencies), or you update `Cargo.lock` by hand. Such a great tooling!
https://github.com/samuelcolvin/watchfiles/pull/267#issuecomment-2094753389
🦀 The first episode of 'Rust in Production' season 2 is live!
https://corrode.dev/podcast/s02e01-curl/
Super excited about talking to @bagder about using Rust in curl!
We’re pleased to announce the release of version 0.10.0 of “domain”, our #rustlang crate for interacting with the #DNS. This release results from the first three months of increased focus on the library, with three full-time #Rust developers and a one-year commitment from @sovtechfund.
We included three major new features: the client side of sending DNS messages, its server counterpart, and the machinery for representing DNS zones. Read all about it in this post. https://nlnetlabs.nl/news/2024/Apr/29/domain-0.10.0-released/
Announcing Freya 0.2 GUI Library
Discussions: https://discu.eu/q/https://freyaui.dev/posts/0.2
Time for your daily dose of #RustLang complaints. Yep, the ecosystem is doing great.
#UV depends on tokio-tar library. Tokio-tar is broken on #PowerPC, doesn't have a bug tracker (!) and seems to be quite dead, with a bunch of PRs ignored since 2022 (last activity mid-2023). Nevertheless, I've filed a PR to fix PowerPC, with little hope that it'll be merged, released and that we could get UV working on PowerPC.
On top of that, it seems that tokio-tar was forked in early 2021 from async-tar. It doesn't seem to have synced the few commits from 2021, and async-tar is dead since late 2021. But at least it has a bug tracker to keep track of how dead it is.
Rewriting stuff in Rust is great. Maintaining it afterwards for the sake of reverse dependencies isn't.
Rust pet project needs constructive criticism
https://github.com/igumnoff/parvati
Discussions: https://discu.eu/q/https://github.com/igumnoff/parvati
🦀 List of Resources to learn Rust - Roadmap From Beginner to Advanced Level
a curated collection of materials designed to assist learners at various stages of their journey with the Rust.
A part of #Rustlang that doesn't get mentioned but is a ridiculous quality of life boon:
dbg!()
Just #[derive(Debug)] on a struct and print it. Suddenly you get insight into what's going on. Very rarely do you need to write your own print.
Insert a dbg in the middle of anything
let diffi = debug!(diffs).iter();
and you get a message with line number and the name of variable:
[src/lib.rs:192:19] diffs = [16, 86, 11]
Not even #Python has that!
Within #deltachat teams and with many collaborating experts and projects around us, we somewhat stubbornly cling to "working code wins" .... But don't forget it's powerful sibling: "maintenable code wins", especially in the longer term. Our automated testing culture, our use of #rustlang at the heart of things and our usability-first focus all help maintenanbility. We don't have the treachery luxury of vc-funding which means we must be a hundred times more economical in our approaches.
Do you type fast? Check out this TUI! 🔥
🏁 **ttyper**: Terminal-based typing test.
🚀 Supports different languages - you can test with Rust keywords!
🎨 Supports configuration and custom styles.
🦀 Written in Rust & built with @ratatui_rs
⭐ GitHub: https://github.com/max-niederman/ttyper
LLMs are the new memory-safety bugs.
There's a good reason that everyone (even the White House!) hates memory safety bugs. Unlike most other code errors, a memory-safety bug allows an attacker to step outside of the abstract machine. When you write C, or any higher-level language, you have a model that has things like structured programming for control flow, object-level abstractions, and so on. A memory-safety bug is, by definition, one that steps outside of this model. A pointer accesses an object that, according to the abstract machine, it should not be able to reach (and which may not even exist in the abstract machine). This can make control flow jump anywhere, tamper with any bit of the program, and so on.
In the last stack of CVEs I reviewed for a project that I'm using, 80% were memory safety but, more importantly, every single one of the ones that ended with arbitrary-code execution started with violating memory safety. Most other bug classes let you explore flows in the program that maybe shouldn't be there, but at least can be reasoned about at the source level.
This is why #RustLang people get so annoyed by all of the 'look, Rust didn't prevent this vulnerability' posts that are cropping up. Yes, Rust is not a magical thing that prevents all bugs, but most of the security bugs that people are finding in Rust programs have behaviour that you can reason about in Rust at the source-code level. In contrast, a memory-safety bug in one component may be exploited in a totally unrelated component that, at the source level, shares no common data or control flow with the component that introduced the bug.
That behaviour is exactly what you get with LLMs. It is impossible to articulate the set of behaviours that an LLM may have, other than that it will consume a sequence of tokens and produce a sequence of tokens. LLMs, like the systems that most engineers abandoned in the 1990s, use in-band signalling and do not separate control and data lines. Both untrusted data and trusted prompts are fed into the same inputs and both have the ability to influence the output. This may be fairly benign if a human is consuming the output (wildly inaccurate or offensive, perhaps), but it's dangerous if a machine is consuming the output and performing actions based on it. As with a memory-safety bug, you must assume that an attacker targeting the LLM can do anything that the LLM is able to do.
The Chrome team popularised the Rule of two (no, not that one): Any program may be no more than two out of: written in an unsafe language, consuming untrusted data, running outside of a sandbox.
I would suggest that anything that incorporates an LLM is treated in exactly the same way as things written in unsafe languages. If it touches untrusted data (e.g. reading your emails, or consuming documents that you did not author) then it must be assumed to be under the control of the attacker and sandboxed. If it's not sandboxed, it must consume only trusted inputs (even then, the output shouldn't be trusted, but it's no more untrusted than any other buggy bit of code).
Creating a #RustLang Custom Target for QEMU #RISCV ... So Rust Apps will build OK for Apache #NuttX RTOS
Source: https://github.com/lupyuen/nuttx-rust-app#rust-custom-target-for-qemu-risc-v-on-apache-nuttx-rtos
I'm excited to announce the new version of **Ratatui**! 🐁
🦀 A Rust library that's all about cooking up terminal user interfaces (@ratatui_rs)
✨ Release highlights: https://ratatui.rs/highlights/v0262/
📢 I'm giving a lightning talk on Ratatui at **Rust for Lunch** tomorrow! (https://lunch.rs/meetups/2024-04-16)
🧀 GitHub: https://github.com/ratatui-org/ratatui
Lol so many ignorants on the recent vulnerabilities about command injection.
Btw, it is not just Rust affected. It affects most langs. Rust is the only one who cares and released a security advisory
I have no personal experiences with it, but it is on my watch list.
I suppose everyone and their grandmother is now using the xz/sshd exploit to further their own agenda, so I am going to take this opportunity to further mine as well.
1. #Autotools are a bad build system. If configure scripts are completely unreadable, there should be no surprise that people won't notice obfuscated malicious code in there, provided that everything else is obfuscated by design.
2. Static linking and vendoring is bad. Do you know why the prompt #security response was possible? Because we just had to revert to older liblzma. We didn't have to check, patch and re-release hundreds of projects. It wouldn't be this easy with #RustLang and cargo.
3. You can blame #OpenSource for being underfunded and open to abuse in core system packages. However, no IT project can be resilient to a sufficiently powerful bad actor, and that it happened to xz is just an incident. Corporate projects aren't resilient to it, neither is proprietary, closed-source software.
So, embrace #Meson, embrace dynamic linking, embrace distribution packaging and donate to open source developers.
I'm now wondering if @rust is a good first #programming language for me to learn? There seems to be an awful lot of projects I could contribute to, if I do! 🤔
🦀 "It is much easier to teach someone to become a good Rust programmer than teach them to be a good C++ Programmer"
https://open.spotify.com/episode/4y1GlQExwA8Qc187ejWAOV
- From "Rust in Production" podcast
- Guest: Micah Wylde from Arroyo
The power is not in the code and not in  #clang or
#clang or  #rustlang, code is simply semantic constructs that make the machine work one way or another. It’s all dead, only the spirit inside you is alive, everything comes to life only in your perception. The romance of #coding is only yours, but limiting yourself to only that means falling into a trap. Life is much more multifaceted, which means you should be multifaceted. You have a spirit that guides and motivates you, take care of it and develop it, train your body and mind. Maybe in ten years the world will turn into complete #cyberpunk, we must not lose ourselves in it and play cool game at the same time... 😉
#rustlang, code is simply semantic constructs that make the machine work one way or another. It’s all dead, only the spirit inside you is alive, everything comes to life only in your perception. The romance of #coding is only yours, but limiting yourself to only that means falling into a trap. Life is much more multifaceted, which means you should be multifaceted. You have a spirit that guides and motivates you, take care of it and develop it, train your body and mind. Maybe in ten years the world will turn into complete #cyberpunk, we must not lose ourselves in it and play cool game at the same time... 😉
Do you use Matrix for chatting? Do you like Vim? I got the perfect tool for you. ✨
📨 **iamb**: A Matrix client for Vim addicts.
💬 Use Vim keybindings for message editing, window navigation, and tab management in your terminal!
🔗 Docs: https://iamb.chat
⭐ GitHub: https://github.com/ulyssa/iamb
🦀 @matrix + @ratatui_rs
#rustlang #tui #ratatui #matrix #client #messaging #vim #neovim #terminal
«Why I chose #Tauri instead of #Electron»
So to say secure #app's that are to run on different #desktop's will in my opinion use #Rust / #RustLang with @TauriApps for development and no longer @electronjs:
🦀 https://scribe.rip/why-i-chose-tauri-instead-of-electron-e67b34f8857d
«EdgenAI – GenAI made Local: Run Generative AI locally, no internet, completely data-private»
I am not a friend of artificial intelligence, but it may happen in the future that I "have to" use it. Do any of you know GenAI, which is developed in Rust, and if so, how is it?
⚡ https://edgen.co
—
#openai #rust #rustlang #nointernet #ai #OpenGPD #llm #opensource #genai #opensource #oss #privacy #data #LLMs #dataprivacy #coding
«Programmiersprache: #Rust-Entwickler fürchten sich vor Komplexität»
Da ich immer noch #RustLang am lernen bin, kann ich den Artikel rel. schlecht einschätzen. Doch #Komplexitat kommt je nach Aufgabe in jeder #Programmierung vor und ist mMn nicht der Sprache abhängig aber das ist nun wieder nur eine #Anwender-Ansicht.
🦀 https://www.heise.de/news/Rust-Entwicklung-Developer-wuenschen-sich-weniger-Tempo-9633317.html
Thank you @andybalaam to make #learn videos about @tweedegolf and for sharing your #Rust exercises to learn the #RustLang:
Rust 101 – Exercises
🦀 https://101-rs.tweede.golf
📺 https://www.artificialworlds.net/blog/2023/09/11/rust-101-1-course-intro/
Rust 101 fans, another video for you:
https://diode.zone/w/9Db2EwKP8ga6A5oaBhripm
https://www.artificialworlds.net/blog/2024/02/19/rust-101-12-traits/
It's all about traits, which describe what a type can do.
«New macOS #Backdoor Linked to Prominent Ransomware Groups:
A newly identified #macOS backdoor written in #Rust / #RustLang appears linked to the prominent #ransomware families Black Basta and Alphv/BlackCat, cybersecurity firm Bitdefender reports.»
I won't say anything more about it, except that it is apparently more #secure than Windows alone, it is not yet protected. Of course everything can be #hack'ed, but it has to reward the attackers.
🔓 https://www.securityweek.com/new-macos-backdoor-linked-to-prominent-ransomware-groups/
«Iced for #Desktop Development in Rust»
Thank you @webbureaucrat for your (older) #blog post explaining how to use #iced in your #Rust project. I am an absolute #RustLang beginner but knowing what can be used for what and how always helps.
⚙️ https://webbureaucrat.gitlab.io/articles/iced-for-desktop-development-in-rust/
The recording of my FOSDEM talk
"The Four Horsemen of Bad Rust Code"
is now online! ▶️🦀⚙️💡🐴
https://video.fosdem.org/2024/h1308/fosdem-2024-2434-the-four-horsemen-of-bad-rust-code.av1.webm
Feedback very welcome!
#rust #rustlang #fosdem #talk #programming
You may find my insights and summary directly on my latest post:
https://gyptazy.ch/misc/fosdem-2024-open-source-conference-brussels-insights/
#opensource #open #freebsd #netbsd #openbsd #foss #debian #linux #rockylinux #python #coding #rust #rustlang #techtalks #openran #illumos #unix #opensolaris #openindiana #omnios #dyson #wifi
The next chapter of Rust 101 is an important little one:
Strings!
https://diode.zone/w/dxQuzYToShEN2rbYhXeo7j
https://www.artificialworlds.net/blog/2024/01/25/rust-101-10-strings/
FreeBSD discusses use of Rust in the base system
https://lists.freebsd.org/archives/freebsd-hackers/2024-January/002823.html
Discussions: https://discu.eu/q/https://lists.freebsd.org/archives/freebsd-hackers/2024-January/002823.html
FreeBSD Considers Making Use Of Rust Within Its Base System
Fish shell 3.7.0 released, the last release branch before the full Rust rewrite
https://github.com/fish-shell/fish-shell/releases/tag/3.7.0
Discussions: https://discu.eu/q/https://github.com/fish-shell/fish-shell/releases/tag/3.7.0
Leading up to a major announcement, @alexband and @benno want to set the stage by laying out our vision for #DNS and our #OpenSource product strategy for the next five years. #Rust #rustlang #MemorySafety https://blog.nlnetlabs.nl/the-next-five-years-of-dns-at-nlnet-labs/
Interesting page: "Why Is SQLite Coded In C" https://www.sqlite.org/whyc.html
...it is possible that SQLite might one day be recoded in Rust. ...
Some preconditions that must occur before....
OK, now I have found a solution (look toots above) using #Rust thanks the tip from @beowulf. Although I briefly shut down #100DaysOfRust, this motivates me to continue learning #RustLang practically. I will something similar to #code but look at @rust for inspiration 🙌
«#Zola: Your one-stop static #site engine – Forget dependencies. Everything you need in one binary.»
Andrea Righi[1] wrote a #LinuxKernel scheduler in #Rust / #Rustlang using sched-ext[2]; he claims he was "'"pretty shocked to see that it doesn't just work, but it can even outperform the default #Linux scheduler (EEVDF) with certain workloads (i.e., gaming):"'"
He shared it on the #birdside: https://twitter.com/arighi/status/1746938387968254371
Github page: https://github.com/sched-ext/scx/
Video: https://www.youtube.com/watch?v=oCfVbz9jvVQ
[1] #Kernel engineer @ Canonical
[2] https://lwn.net/Articles/922405/
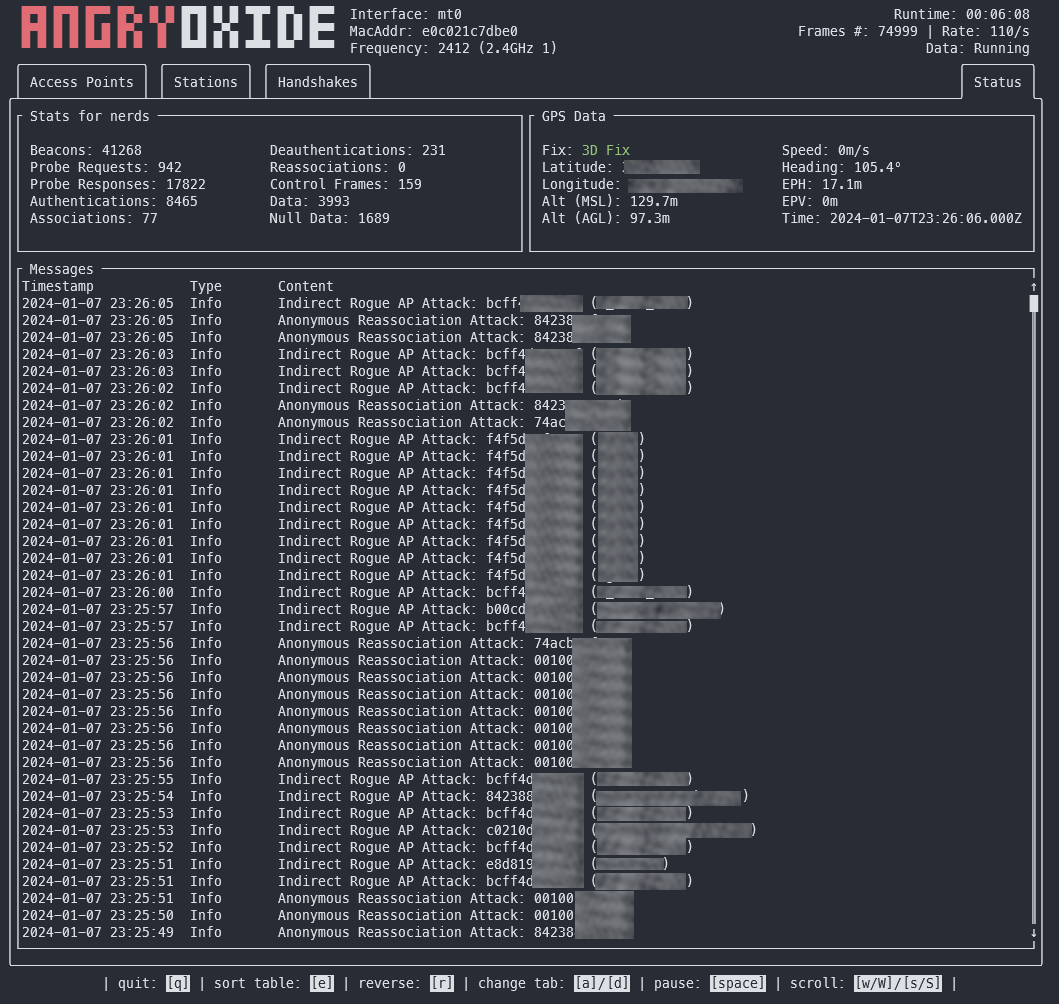
Came across a terminal-based network security tool today! 🕵️♂️🔒
🦀 **AngryOxide**: 802.11 Attack Tool
🐭 Written in Rust / Built with @ratatui_rs
⭐ GitHub: https://github.com/Ragnt/AngryOxide


 🙀🚂🐧
🙀🚂🐧