sshd(8) split into multiple binaries https://www.undeadly.org/cgi?action=article;sid=20240517092416 #OpenBSD #ssh #sshd #sshd-session #privsep #security #secureshell
Wer ist "Jia Tan"? Eine interessant zu lesende Spurensuche von
@marcel anhand von technischen Indizien zu Zeitzonen, Verhalten, Motive, Aufwand.
Wir sind dieses Wochenende nur durch unglaubliches Glück und extrem knapp an wohl einer der grössten Katastrophen rund um die globale IT-Sicherheit vorbeigeschrammt.
Phuh! Doch — was ist eigentlich passiert? Wie konnte das überhaupt geschehen? Und was können (und müssen) wir tun, um dies zukünftig zu vermeiden?
Und: Danke an die ganzen IT-Helden, die dies an diesem langen Wochenende für uns getan haben.
#xz #lzma #ssh
https://dnip.ch/2024/04/02/xz-open-source-ostern-welt-retten/
Der Angriff hatte zum Ziel, Abermillionen von Servern weltweit für die unbekannten Angreifer zu öffnen. Was diese mit den Früchten der Vorbereitung der letzten 3 Jahre dann hätten erreichen wollen, das werden wir wohl nie erfahren. Aber die potenziellen Auswirkungen auf Abermillionen von Nutzerinnen, ihren Daten aber auch die Wirtschaft und Stabilität von ganzen Ländern hätten dramatisch werden können.
#xz #lzma #ssh
https://dnip.ch/2024/04/02/xz-open-source-ostern-welt-retten/
Durch Good-Cop/Bad-Cop-Taktiken wurden Softwareentwickler dazu gedrängt, subtil versteckte Sicherheitslücken einzubauen. Wie können wir das zukünftig vermeiden?
.
1️⃣ Vereinfachung/Reduzierung von Programmen und Abhängigkeiten
2️⃣ Mehr Wertschätzung und Unterstützung für die Open-Source-Entwickler
3️⃣ Bessere Kontrolle, aber ohne Belastung für die Entwickler
4️⃣ Angewandtere Ausbildung
Was sind eure Ideen dazu? Freue mich auf Feedback!
#xz #lzma #ssh #FOSS #FLOSS #OSS
https://marcel-waldvogel.ch/2024/04/02/wie-die-open-source-community-an-ostern-die-it-welt-rettete/
«Die Feiertage. Die ganzen IT-Abteilungen feiern mit der Familie… Die ganzen IT-Abteilungen? Nein! Eine von unbeugsamen Open-Source-Enthusiasten bevölkerte Mailingliste hört nicht auf, den Eindringlingen Widerstand zu leisten.»
#xz #xzbackdoor #lzma #ssh
https://dnip.ch/2024/04/02/xz-open-source-ostern-welt-retten/
Worked on #DistDetect (https://github.com/xtaran/dist-detect) today, added #OpenSSH signatures for #Fedora (21-40; source: https://bodhi.fedoraproject.org/updates/?packages=openssh) and for #openSUSE / SLES (11-15; source: https://software.opensuse.org/package/openssh) confirmed by some real-life examples, as well as some other maintenance chores.
While digging through @shodan results for examples I found a host with OpenSSH 3.4p1 and "Apache/1.3.29 (Linux/SuSE)", i.e. a SLES 8.1 from 2002. 🙈
Every version of the PuTTY tools from 0.68 to 0.80 inclusive has a critical vulnerability in the code that generates signatures from ECDSA private keys. Tthe effect of the vulnerability is to compromise the private key https://www.chiark.greenend.org.uk/~sgtatham/putty/wishlist/vuln-p521-bias.html #infosec #security #ssh #opensource #linux #unix #windows
We've released #PuTTY version 0.81. This is a SECURITY UPDATE, fixing a #vulnerability in ECDSA signing for #SSH.
If you've used a 521-bit ECDSA key (ecdsa-sha2-nistp521) with any previous version of PuTTY, consider it compromised! Generate a new key pair, and remove the old public key from authorized_keys files.
Other key types are not affected, even other sizes of ECDSA. In particular, Ed25519 is fine.
This vulnerability has id CVE-2024-31497. Full information is at https://www.chiark.greenend.org.uk/~sgtatham/putty/wishlist/vuln-p521-bias.html
NEW VIDEO - How can I slow down the attacks on my FreeBSD Server?
#FreeBSD #Opensource #SSH #unix #garyhtech
https://youtu.be/Jh_roKrqGiU?si=cCa9CK1utw2m30zs via @YouTube
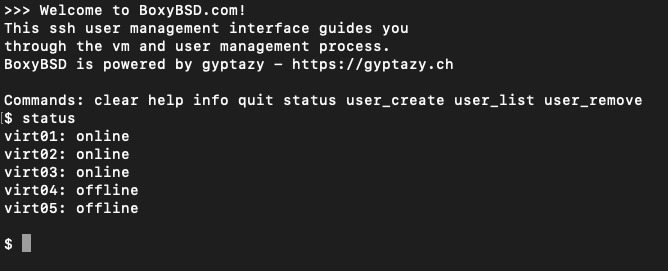
But it also needs something like a self-service portal in long-term. However, for the website I stick to my self-written #manpageblog engine - I guess that fits pretty will here when it's only about serving #FreeBSD, #OpenBSD & #NetBSD.
This being said, I don't want to write a self-service portal for the web and thought about a #ssh service where you just login and can perform several actions like PTR, snapshots, system reset etc.
Currently, I only implemented the user management from an "admin" perspective. A sandbox style can be seen here:
ssh -p 2222 boxybsd@2001:470:54d7:1337::2
Password: create
It's a self-written sshd alike service which communicates with the API and some other bins. Die user login can be done by pub key and pw auth. Feel free to give it a try, it's a sandbox mode on a sandbox vm.
@mttaggart Does this mean that one should never allow #ssh inward as #root? This thread seems to say ssh as root should be inherently forbidden. https://stackoverflow.com/questions/18395622/remote-login-as-root-in-ubuntu #xz #CVE_2024_3094
Uncommenting the "block in all", sending a pfctl -f /etc/pf.conf - noting in that precise moment that I didn't explicitly pass ssh - being closed out of my own server...done! ✅
#Networking #SysAdmin #Firewall #Security #SSH #ServerManagement #FreeBSD #OpenBSD
Eek. Apparently liblzma (part of the xz package) has a backdoor in versions 5.6.0 and 5.6.1, causing SSH to be compromised.
https://www.openwall.com/lists/oss-security/2024/03/29/4
This might even have been done on purpose by the upstream devs.
Developing story, please take with a grain of salt.
The 5.6 versions are somewhat recent, depending on how bleeding edge your distro is you might not be affected.
@jhx For writing some kind of "howto", I'll have to find a sane scope ... otherwise there would be just too much to describe I guess 😮
I could of course assume you already have
- network segmentation with a #DMZ
- a working "domain" setup with a directory and #DNS (e.g. #samba, but could be #OpenLDAP with #bind9 as well)
- (virtual) machines providing #RDP (with #xrdp in case of #Linux or #FreeBSD)
- a working mechanism to distribute X.509 #TLS #certificates (I request them from #letsencrypt using #uacme and distribute them with simple shell scripts using special-purpose restricted #SSH keys)
With all that in place, it would "just" be describing the setup of #guacamole in a #FreeBSD #jail, enabling #TLS on all connection paths...
@jhx For writing some kind of "howto", I'll have to find a sane scope ... otherwise there would be just too much to describe I guess 😮
I could of course assume you already have
- network segmentation with a #DMZ
- a working "domain" setup with a directory and #DNS (e.g. #samba, but could be #OpenLDAP with #bind9 as well)
- (virtual) machines providing #RDP (with #xrdp in case of #Linux or #FreeBSD)
- a working mechanism to distribute X.509 #TLS #certificates (I request them from #letsencrypt using #uacme and distribute them with simple shell scripts using special-purpose restricted #SSH keys)
With all that in place, it would "just" be describing the setup of #guacamole in a #FreeBSD #jail, enabling #TLS on all connection paths...
Let's follow the agenda https://datatracker.ietf.org/meeting/119/materials/agenda-119-alldispatch-05
First, #SSH v3
(I hear people chat and laugh during the reminder of the Code of Conduct.)
Question for the git and infosec crowd:
Do you prefer fine-grained personal access tokens (PAT) or secure shell (SSH) authentication for GitHub etc.? Do you have strong feelings about either?
Happy to be pointed to additional resources, my initial searches just turned up vague and poorly LLM-written blog posts...
TIL that for some reason unlike on Linux, FreeBSD, and even Haiku a #ssh session on Mac doesn’t setup the path automatically when you execute a command on start.
So if you want to launch tmux on Mac from ssh you must source your profile first like this (otherwise it won’t find tmux in the homebrew path):
ssh user@192.168.0.33 'source ~/.zshrc; tmux new-session -A -s "SessionName" '