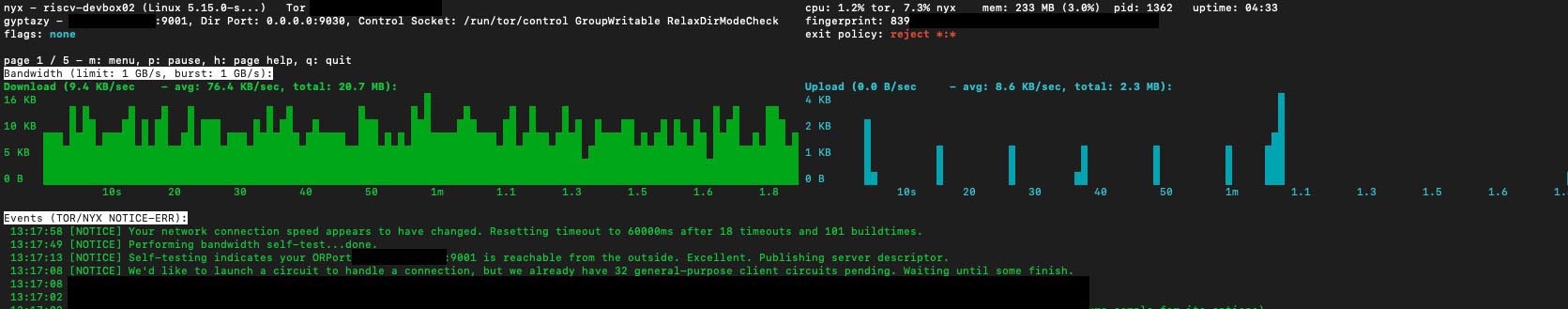
Dell API abused to steal 49 million customer records in data breach | …an example of poor security through lack of both rate limiting & behavioural modelling
<div class="addtoany_share_save_container addtoany_content addtoany_content_bottom"><div class="a2a_kit a2a_kit_size_24 addtoany_list" data-a2a-url="https://alecmuffett.com/article/109806" data-a2a-title="Dell API abused to steal 49 million customer records in data breach | …an example of poor security through lack of both rate limiting & behavioural modelling"></div></div>Once they gained access to the portal, Menelik told BleepingComputer they had created a program that generated 7-digit service tags and submitted them to the portal page starting in March to scrape the returned information.
As the portal reportedly did not include any rate limiting, the threat actor claims they could harvest the information of 49 million customer records by generating 5,000 requests per minute for three weeks, without Dell blocking the attempts.
I can confidently diagnose #betterhelp as sociopaths.
Promised therapy customers privacy...then gave their mental health info to advertisers.
Victims get less than ten bucks each.
Company made billion+ in revenue last year alone.
In a just society with good privacy laws, they'd face existential civil & criminal consequences.
#therapy #psychology #privacy #psychotherapy #mentalhealth #telehealth #medicine #HIPAA #surveillancecapitalism #advertising #facebook #meta
#ProtonMail Discloses User Data Leading to Arrest in Spain
「 The core of the controversy stems from Proton Mail providing the Spanish police with the recovery email address associated with the Proton Mail account of an individual using the pseudonym ‘Xuxo Rondinaire.’ This individual is suspected of being a member of the Mossos d’Esquadra (Catalonia’s police force) and of using their internal knowledge to assist the Democratic Tsunami movement 」
https://restoreprivacy.com/protonmail-discloses-user-data-leading-to-arrest-in-spain/
GrapheneOS version 2024050700 released:
https://grapheneos.org/releases#2024050700
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/12566-grapheneos-version-2024050700-released
GrapheneOS version 2024050300 released:
https://grapheneos.org/releases#2024050300
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/12485-grapheneos-version-2024050300-released
From this week's Linux Update: Matthias Wübbeling shows you how to protect your data and operating system from prying eyes with @veracrypt https://www.linux-magazine.com/Issues/2024/279/VeraCrypt #encryption #VeraCrypt #security #privacy #containers #TrueCrypt #data
Reproducible builds - pros/cons
Instructor allowed me to quote his take on Pros and Cons of reproducible builds. Because, i found this very informative i want to share with others.
Original author: Nathan House (Station X)
"Reproducible builds involve a compilation process that generates the same binary or executable output for a given source code, regardless of the building environment. This approach offers various pros and cons when it comes to security, privacy, and anonymity.
Pros:
1. Trustworthiness: Reproducible builds ensure that the released binary is built from the published source code, allowing users to trust the software without having to compile it themselves.
2. Tamper detection: Any attempts to introduce backdoors or malware during the build process can be detected, as the output can be verified against the expected result.
3. Collaborative verification: Multiple parties can independently verify the builds, increasing confidence in the software's integrity.
4. Supply chain security: Reproducible builds can help mitigate supply chain attacks by ensuring the integrity of the code throughout the development, build, and distribution process.
Cons:
1. Increased complexity: Implementing reproducible builds can be complex and time-consuming, requiring consistent build environments and careful management of dependencies.
2. Limited scope: Reproducible builds only ensure the integrity of the build process and do not guarantee that the source code is free of vulnerabilities or malicious code.
3. False sense of security: Users may assume that reproducible builds imply that the software is entirely secure, while they only guarantee that the build process is consistent and hasn't been tampered with.
4. Overhead: Maintaining a reproducible build environment may introduce additional overhead for developers, potentially slowing down the development process.
Overall, reproducible builds can significantly enhance security, privacy, and anonymity in the software development process. However, their implementation requires careful planning and may introduce challenges and complexities that need to be managed effectively."
**BSD Mail Project Update!**
Hello everyone! I wanted to share some exciting updates about the development of BSD Mail, our privacy-focused email service designed with robustness, security, and transparency in mind. Here’s a deep dive into the technical choices I've made, focusing on my use of open source solutions and open protocols:
🌍 **Servers & Location**
- We're running on two physical servers:
- One hosted by OVH in France
- Another by Hetzner in Germany
- Both servers operate on FreeBSD with NVMe drives in a ZFS mirror configuration for speed and data integrity.
🔒 **Virtualization & Security**
- We utilize jails on both servers to ensure isolated environments for different services, managed via BastilleBSD. On one server, jails are set up directly on the hardware, whereas the other server employs nested jails.
- Each server hosts a bhyve VM running OpenBSD with OpenSMTPD for handling SMTP duties securely.
🔗 **Networking**
- A Wireguard setup connects the two servers, facilitating routing capabilities so that jails and VMs can communicate seamlessly, supporting both IPv4 and IPv6.
📧 **Email Services**
- **Dovecot** is configured for maildir replication across the servers using Dovecot sync, ensuring email availability and redundancy.
- **Rspamd** instances are tied to local KeyDB jails, set up in master-master replication for consistent and reliable spam detection and greylisting.
- **ClamAV** runs in corresponding jails for virus scanning, maintaining a high level of security.
- **SOGo** provides a web interface for email management, connected to MySQL databases in master-master replication to handle sessions and authentication smoothly.
💾 **Data Management**
- Email data is stored on separate, encrypted ZFS datasets to secure emails at rest.
- MySQL databases are used for storing credentials and managing sessions for SOGo, also in a master-master replication setup. Importantly, all passwords are securely hashed using bcrypt, ensuring they are salted and safe.
🔎 **Monitoring & Reliability**
- Our DNS is managed through BunnyNet, which continuously monitors our server status. Should one server—or a specific service—become unavailable, DNS configurations are dynamically adjusted to avoid directing users to the affected IP until full service is restored.
🌐 **Commitment to Open Source and Open Protocols**
- Every component of BSD Mail is built exclusively using open source software and open protocols. This commitment is crucial for ensuring data freedom and the reliability of the solutions we use.
This setup not only emphasizes our commitment to privacy and security but also our dedication to maintaining an open and transparent platform.
We're excited to bring you a service where your privacy, data integrity, and freedom are prioritized. Stay tuned for more updates!
#BSDMail #OpenSource #Privacy #FreeBSD #OpenBSD #EmailHosting #Email
Today I've been really busy and I'm exhausted, but I wanted to share the "gem" of the day.
A colleague (whom I've never spoken to before) calls me and explains that they need to connect a client's server with their management system. To communicate, the client's server needs to be reachable via telnet. I explain that I can't open telnet to the world, but if necessary, I can set up a VPN of their choice (Wireguard, OpenVPN, even Zerotier if it's helpful) and grant telnet access through the VPN. Not ideal, but better than nothing...
That said, the colleague attacks me: "Here you are, with these VPNs - don't you understand they're used to spy on us? Governments intercept all VPNs to steal our personal data." I try to clarify that I may not have explained myself well and that I don't mean using the famous commercial VPNs, but a private VPN access to allow the two machines to communicate securely. No luck: "Haven't you realized yet? Every time we open a VPN, they know and intercept us."
Frankly, I was speechless...
#VPN #Privacy #Security #Misconceptions #IT #SysAdmin #ITHorrorStories
HiddenVM: use any desktop OS without leaving a Trace - An open-source Linux application that allows you to run Oracle's open-source VirtualBox software on the Tails operating system #Privacy https://github.com/aforensics/HiddenVM
We fool ourselves if we think governments aren't spying on their citizens. It's one of those things that snuck in and stayed, and is not going away but expanding.
"Poland's prosecutor general says previous government used spyware against hundreds of people"
"Poland’s prosecutor general has told the parliament that powerful Pegasus spyware was used against hundreds of people during the former government in Poland"
Big Tech embraces Passkey (tech to replace passwords) to maintain their walled Gardens - Post by Son Nguyen for @protonprivacy #Privacy https://proton.me/blog/big-tech-passkey
From a coworker at ${DAYJOB}:
For anyone who is buying the Humane AI PIN, be careful. Their terms of use contains a clause that gives them a license to all the data you link to the service:
4.2 Ownership. For purposes of clarity, you retain ownership of your Submissions. For each Submission, you hereby grant to us an irrevocable, unlimited, worldwide, royalty-free, fully paid-up, perpetual, sublicensable (through multiple tiers), and non-exclusive license, without any additional consideration to you or any third party, to copy, reproduce, adapt, modify, edit, distribute, translate, publish, perform and display (publicly or otherwise), create derivative works of, and otherwise use, analyze, and exploit such Submission, in any format or media now known or hereafter developed, and for any purpose, to the fullest extent allowed by Law.
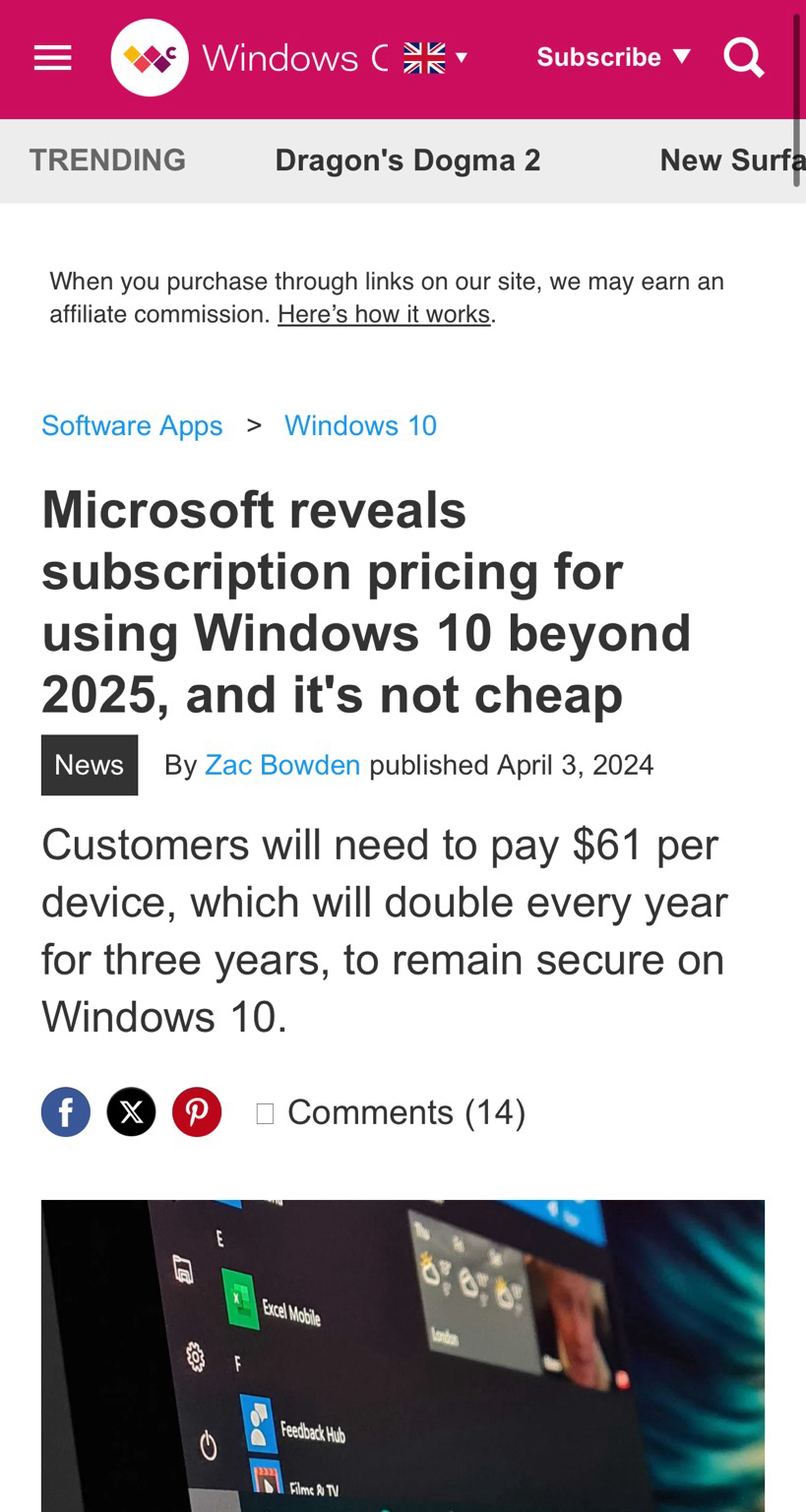
Microsoft reveals subscription pricing for using Windows 10 beyond 2025, and it's not cheap. Customers will need to pay $61 per device, which will double every year for three years, to remain secure on Windows 10. If you just do shopping or social media you can use alternative os like Ubuntu, Mint, or pop os for your older computer instead of jumping to windows 11. Also regardless of windows 10 or 11 prices you will still get Ads in Windows 😂 #linux #privacy #security Choose wisely
「 Prosecutors also allege that Facebook violated the United States Wiretap Act, which prohibits the intentional procurement of another person’s electronic communications. Onavo could also be considered straight spyware, but also seems to fall under the definition of wiretapping, according to prosecutors 」
https://gizmodo.com/project-ghostbusters-facebook-meta-wiretap-snapchat-1851366093
Le service de VPN public en accès libre de FDN (association French Data Network) @FDN fait peau neuve #VPN #Privacy https://www.fdn.fr/notre-vpn-en-acces-libre-fait-peau-neuve
15 million users in the Fediverse, now.
No ad-blocker needed.
Zero ads.
My data stays on my server.
Interactions are genuine, driven by people's desire, not an algorithm pushing for conflict to boost engagement (and ad sales).
Nobody's here just because it's trendy. If you're here, you want to be here.
The best social media experience I've had in years.
Thank you to all of you, among these 15 million accounts, who have helped make this a wonderful place to be.
#Fediverse #Privacy #NoAds #GenuineInteractions #Decentralized #ThankYou #Mastodon
Ouch! AMS-IX is hit bad here 🤦♀️ 🥺 👩💻
“The Netherlands hosts some of the world’s largest internet exchanges. This obliges us to make the best use of these exchanges for our national security. With the Temporary Cyber Act, we will make optimum use of the data carried on our cables to protect The Netherlands against Russian and Chinese hackers” – Dutch government announcement
https://berthub.eu/articles/posts/dutch-intelligence-and-security-law/
🆕 blog! “Can you trust ProtonApps.com?”
I've recently signed up to the privacy-preserving service Proton. All the email, calendar, drive, VPN, and other services seem to hang off the proton.me domain. I wanted to download the Android apps to my phone - without using the Google Play Store. The VPN app is on F-Droid but none of the others are. So, […]
👀 Read more: https://shkspr.mobi/blog/2024/03/can-you-trust-protonapps-com/
⸻
#OpenSource #privacy #Proton
Well it seems that Docusign, the largest online signing service for mostly confidential documents... is using your documents to train it's AI regurgitation machines:
https://mastodon.social/@gvwilson/112012277852906749
Thankfully it seems that there's also an open source, self hostable alternative in Documenso:
Https://Documenso.com
Please boost and talk to your org about switching today! (I'm not affiliated)
«EdgenAI – GenAI made Local: Run Generative AI locally, no internet, completely data-private»
I am not a friend of artificial intelligence, but it may happen in the future that I "have to" use it. Do any of you know GenAI, which is developed in Rust, and if so, how is it?
⚡ https://edgen.co
—
#openai #rust #rustlang #nointernet #ai #OpenGPD #llm #opensource #genai #opensource #oss #privacy #data #LLMs #dataprivacy #coding
I'm not so familiar with #AI and security on the #Internet that I really have a #clue. That's another reason why articles like this are very good for informing me and explaining it to customers. #WebSec is more than just #password and #secrecy.
«Post Quantum Cryptography: Why We Need Resistant Encryption NOW.
Quantum-resistant or post-quantum #cryptography is our best bet against attacks from upcoming quantum computers to increase #security and #privacy.»
– @Tutanota
Consumer software, LOL. They are blaming a "third-party caching library", but really this is (as always) failure to catch a corner case somewhere in their code. #Wyze #leak #cybersecurity #privacy
Yet another site with privacy guides
"The Privacy Raccoon"
https://privacy.awiki.org/about.html
"We’re a group of privacy activists and computer wizards that were disappointed with “mainstream” privacy sites like PrivacyGuides.org, PrivacyTools.io, Techlore, etc. These sites recommend solutions that are considered spyware and even privacy violators.
...
They are also sold to sponsors, prioritizing money over their readers’ privacy and freedom.
These sites have received a ton of attention recently. We believe that there is an increasing interest in digital privacy. That’s why we decided to create a privacy resource that truly respects your privacy and freedoms."
I just discovered #SimpleLogin a product of @protonmail
It's a powerfull and amazing tool to protect your email addresses.
Easy to manage from Pass or from dashboard on simplelogin.io
#Privacy #Proton #Pass
Who is the real Owner of your Data?
https://my-notes.dragas.net/posts/2024/who-is-the-real-owner-of-your-data/
In #SouthAfrica at the moment, there's currently a bill on the table which would allow government far-reaching ability to override regular citizens' #privacy by conducting bulk #surveilance.
Some people are colloquially calling it the "#spying bill": https://techcentral.co.za/south-africa-spying-law-is-deeply-flawed/239456/?utm_source=Mastodon
Dear friends of the #BSDCafe and the #Fediverse,
Bytedance is connecting to our server every few seconds. As I don't understand why and, more, I've already had problems with their rude behaviour, I've added this rule to nginx.conf:
# case sensitive matching
if ($http_user_agent ~ (Bytespider)) {
return 444;
}
# case insensitive matching
if ($http_user_agent ~* (bytespider)) {
return 444;
}
They should be out, at least for now.
#Privacy #Security #WebScraping #OnlinePrivacy #FediverseSecurity
I don't like myths, so who study #security and #privacy topics ... and who should learn security and privacy?
---------------------------
- technically minded people
- people concerned about hackers, cyber criminals, malware and viruses
- people that wants to share information anonymously
- people that wants to keep communication and personal information private
- people interested in technology and the internet
- people concerned about government and corporate spying
- security professionals
- students studying IT or security
- freedom fighters
- political or religious dissidents
- journalists
- businessmen or women where security, privacy and anoymity matters
- law enforcements officers and agents
- high profile individuals
- whitle blowers
- anonymous bloggers
- anyone who has an interest in security, privacy and anonymity
Celebrities using public airspace for private aircraft have no reasonable expectation to #privacy, period.
Actually, I don't use an ad blocker. I use uMatrix, so, I can decide whose cookies I accept, and whose scripts I run on my computer.
If a company wants to display static adverts on their site, that's fine by me. What isn't acceptable are scripts which allow third-parties to track me, all over the Internet. I'm not willing to compromise my privacy.
So nice to see my system wide AdBlocker for Ubuntu Touch featured in OpenStore https://open-store.io/app/uadblockng.liohmoeller
#Ubuntu #UbuntuTouch #ubtouch #OpenStore #Linux #Adblock #Privacy #Adblocker











 Why I use Firefox
Why I use Firefox